Application
Definition
Application is the main synchronization configuration entry point. An "Application" conceptually designates a remote system, external to Synchronization Service, exposing a repository of accounts (or organizations), such as a LDAP directory, or a CSV file.
Usually an Application is configured to perform either “inbound” operations, such as importing a CSV file, or “outbound” operations, such as provisioning an LDAP directory. Technically, the same Application could be configured to perform both inbound and outbound operations, but this is a rare functional case, because most of the time there is a single “authoritative side”. For example, a HR CSV file is the unique “source of truth” to create or update IM Identities, and in turn IM Identities are the source of truth to create or update accounts in a LDAP directory.
The Application namely defines “attribute mappings”, i.e. how to map an IDM object’s attributes (such as a last name) with the attributes of an object belonging to a remote system, such as the columns of a CSV file or the attributes of an LDAP account.
Attribute mapping rules may vary according to the type of an IDM object, e.g. for an IDM object of type “employee” the mapped attributes could differ from an IDM object of type “partner”.
An Application's population may thus be divided into several IDM Object Types, hence the possible diversification, within an Application's configuration, of sub-configurations per Object Type, as shown in the schema below:
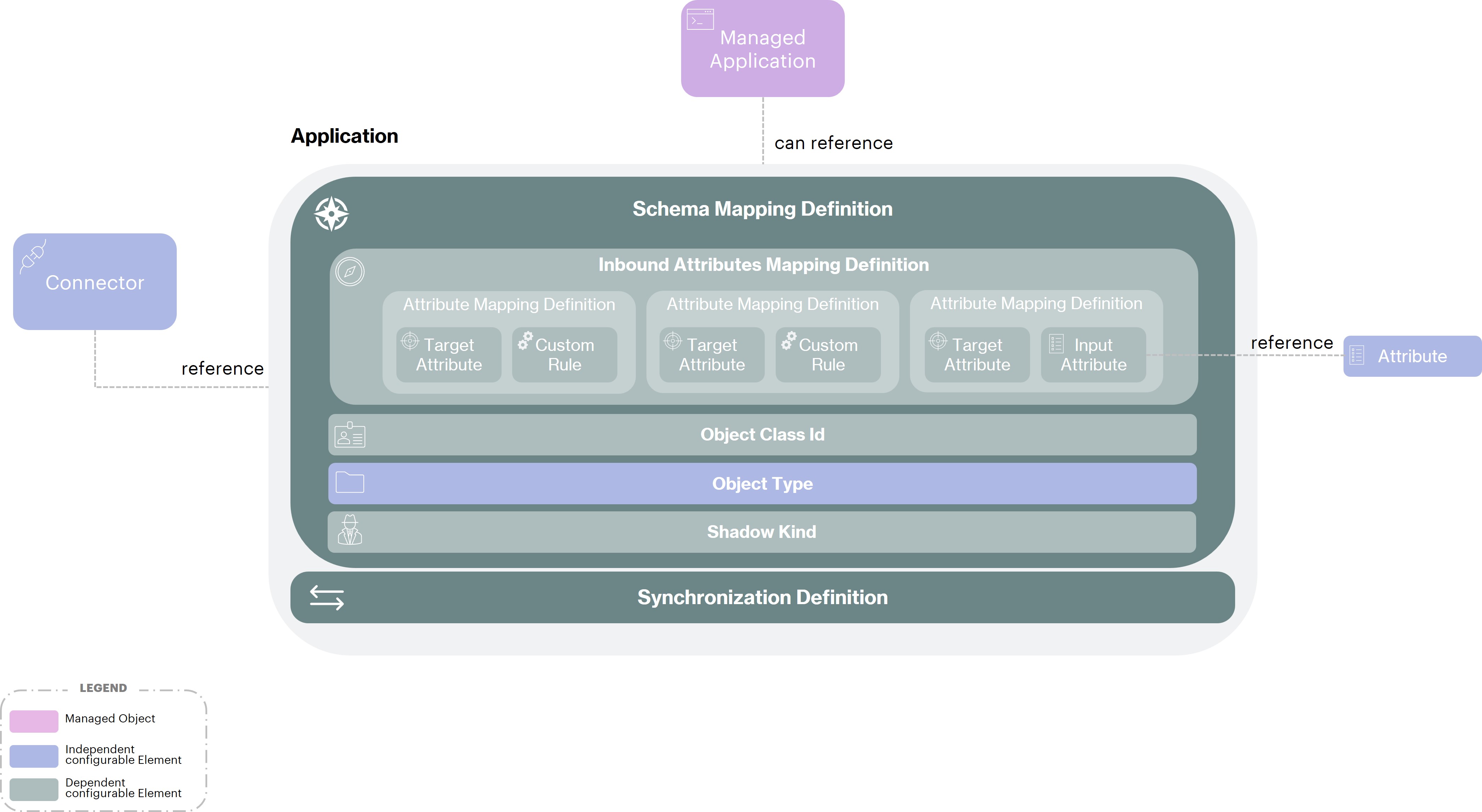
Among all sub-configurations segregated by Object Type, a single sub-configuration may have a null Object Type. This is the “default” sub-configuration, applied when no sub-configuration matching a given Object Type was found.
In the above schema, the term “Shadow” designates remote accounts known and registered into the Synchronization Service. A “Shadow” is thus the “projection” of an IDM object on a remote system, according to the configured attribute mapping rules.
In the same way as an IDM object, which can be of kind “Identity” or “Organization”, a Shadow has also a kind:
Shadow Kind | Corresponding IDM Object Kind | Note |
|---|---|---|
ACCOUNT | IDENTITY | |
ORGANIZATION | ORGANIZATION | |
RESOURCE | RESOURCE | |
ROLE | ROLE | |
ROLE_PUBLICATION | ROLE_PUBLICATION | |
ENTITLEMENT | N/A | An “Entitlement” is a generic representation of an Application-side asset, such as a group, role, privilege, or access right. It is not mapped to an IDM object. |
The term “Object Class Id” designates the technical class of an object on a remote system. For example, it can be inetOrgPerson for the provisioning of an LDAP directory. Accounts to sync are searched on the remote Application using this class criterion, even for the CSV Connector case when reading the CSV file.
The Object Class Id is fixed by convention to __ACCOUNT__ for the CSV Connector, the SQL Connector and the SAP Connector. The __ACCOUNT__ Object Class Id shall not be confused with the ACCOUNT Shadow Kind. A CSV file can indeed contain Organizations, whereas the Object Class Id remains fixed to __ACCOUNT__, because that’s a technical convention of the CSV Connector.
The triplet [Object Class Id, Shadow Kind, Object Type] enables to identify a configuration in a non-ambiguous way, for both inbound and outbound operations. This triplet must be unique for a given sub-configuration.
Configuration
You can access the Application configuration :
by clicking on "Synchronization" → "Applications"
by clicking on "System" → "Configurations"->”Synchronization Service” and perform an import/export.
Properties
The main configuration elements are :
Property Name | Type | Mandatory | Description |
|---|---|---|---|
id |
| YES | The Application identifier. |
name |
| YES | The Application name. |
description |
| NO | The Application description. |
citadelApplicationId |
| NO | The identifier of the Memority application, which enables to map a Memority application to a Synchronization service application. If not specified, it is supposed that Memority references the application directly using the |
connectorId |
| YES | The identifier of a Connector Definition. |
- | YES | The configuration of the inbound synchronization. | |
- | YES | The configuration of attribute mappings (inbound or outbound). |
synchronizationDefinition properties
The Synchronization Definition configures the inbound side, i.e. the synchronization behaviour when performing reconciliation, import of live synchronization tasks. It defines:
how to map an application account to an Object Type, via the Object Type Resolution Definition
how to perform the correlation process to determine a synchronization situation, via the Correlation Definition
how to react to a synchronization situation, via a Synchronization Reaction Definition
In fact, the correlation and reaction are configurable per IDM Object Type. Thus, the Synchronization Definition contains a list of Object Synchronization Definition, one per target Object Type.
If the Object Type is configured to null, then the Object Synchronization Definition is considered the default one.
Property Name | Type | Mandatory | Description | Values (default value in bold) |
|---|---|---|---|---|
- | YES | The configuration enabling to resolve the target Object Type from an application account properties. | - | |
objectSynchronizationDefinitions | - | YES | The list of inbound synchronization configurations per Object Type. This list must contain at least one element. | - |
objectTypeMigrationAllowed |
| NO | Whether migrating from one Object Type to another is allowed or not (for example from "partner" to "employee"). This is a safeguard against unwanted type migrations that could be involuntarily triggered by inaccurate information within data to import. | true, false |
objectTypeResolutionDefinition properties
An account belonging to a remote application must be "transposed" to an IDM object. Thus the target IDM object type must be determined, such as "employee" or "partner", from the account properties. This is achieved via an Object Type Resolution Definition. It configures the object type resolution process according to a list of Object Type Assignment Rules. An object type is associated with each rule. The first matching rule wins; the rule's object type is then assigned. If no rule matches, a default IDM object type is assigned. Each rule is configured using a strategy, among 2 possible strategies (one and only one strategy must be chosen for each rule):
simple object type assignment strategy: the most basic configuration, suitable for simple needs. If the value of an account attribute matches a configured regex, the rule matches
custom object type assignment strategy: the most flexible configuration, meant to answer complex business cases. It is based on the execution of a custom Groovy script that must return a Boolean value, indicating whether the rule matches or not
Determining early the target IDM object type is essential because synchronization and attribute mapping settings can be configured per IDM object type. Once the target object type is known, then the other appropriate synchronization settings can be applied during the synchronization process.
Property Name | Type | Mandatory | Description |
|---|---|---|---|
defaultObjectTypeId |
| YES | Object Type that is assigned by default when no assignment rule matches, e.g. "employee". |
| NO | Mutually exclusive with custom Assignment Rule. The Object Type of the first matching rule is assigned. If this list is empty then default Object Type Id will prevail. | |
customAssignmentRule |
| NO | Mutually exclusive with assignment Rules. A Compute Rule returning the Object Type as a String, which may be null. If null then default Object Type Id will prevail. |
assignmentRule properties
The configuration of a rule determining whether or not an Object Type may be assigned to an account.
Property Name | Type | Mandatory | Description |
|---|---|---|---|
objectTypeId |
| YES | The Object Type assigned when the rule matches, e.g. "partner". |
- | YES | The rule matching condition. |
objectSynchronizationDefinitions properties
The inbound synchronization configuration for a specific Object Type (such as "employee").
Property Name | Type | Mandatory | Description |
|---|---|---|---|
name |
| NO | An optional name only used to enhance the configuration display in the admin console GUI. |
objectType |
| NO * | The target Object Type (as a simple String) such as "employee", "partner", etc. If not specified then the default type will apply as configured in Object Type Resolution Definition. (*) Among the list of Object Synchronization Definitions, only one is allowed to have a null object Type field. All object Types may be non null, but there cannot be more than one null object Type. |
objectClassId |
| YES | The class of objects to search on the external application: "inetOrgPerson" for LDAP, "__ACCOUNT__" for CSV, "Identity" for Mongo Collection,etc. It must be coherent with |
shadowKind |
| YES | The kind of Shadow corresponding to the technical Must be coherent with |
enabled |
| NO | Whether this synchronization configuration is enabled or not (true by default). |
- | YES | The correlation configuration used to determine the owner of an application account. | |
| NO | The list of reactions to apply when a synchronization situation occurs. The list may be empty but this is not recommended. | |
- | NO | If defined it prevails on the above standard reaction Definitions | |
customAction |
| NO | A Compute Rule Definition, it must be defined if a This feature is mainly used to generate a custom patch for the By convention, if the rule execution returns A example of custom Action script :
CODE
|
correlationDefinition properties
Correlation
Correlation is a mechanism enabling to identify potential IDM owner(s) of a given application account. The Correlation process takes information from the account and constructs a search query. This query is then used to locate IDM owner(s). The result of the correlation process is categorized into a synchronization situation as explained in the previous sections.
Number of IDM objects found after correlation | Synchronization situation |
|---|---|
0 |
|
1 |
|
> 1 |
|
The Correlation Definition configures the correlation process, according to 2 possible strategies (one and only strategy must be chosen):
simple correlation strategy: the most basic configuration, suitable for simple needs. The value of one or more attributes of an account are simply compared with the attribute(s) of the candidate IDM objects. An optional Compute Rule may be evaluated in between to transform an account's input attribute before matching it with an IDM object attribute. The Compute Rule will be typically implemented with a Groovy script
custom correlation strategy: the most flexible configuration, meant to answer complex business cases. A Compute Rule is evaluated to produce a Correlation Result. The Compute Rule will be executed by a Groovy script performing the complex business search(es) using a Object Finder available in the Groovy context (more on that later)
Optional correlation metadata may be recorded by a custom Groovy script during the correlation process, to keep track of information that will be later helpful during the inbound attributes mapping step, namely to conditionally map some attributes or not when executing custom mappings also implemented by Groovy scripts. This will be detailed in a later section about crafting custom Groovy scripts.
The correlation configuration used to determine the IDM owner of an application account.
One and only one correlation strategy must be configured, among the 2 possible strategies.
Property Name | Type | Mandatory | Description |
|---|---|---|---|
- | NO | Simple attribute(s) value(s) comparison: search IDM objects based on one or more attribute values. | |
- | NO | Evaluation of a custom Groovy Script, performing the IDM search, and producing a |
simpleCorrelationStrategyDefinition properties
The value of one or more attributes of an application account are compared with the attribute(s) of the candidate IDM objects.
A SearchExpression is built using the given attribute mappings (see AttributeCorrelationDefinition below).
If several mappings are provided (e.g. for "login" and "email") then they are AND ed together such as: login=jdoe AND email=john.doe@acme.com.
If an attribute is multi-valued then the attribute values arORed together such as: login=jdoe AND (email=john.doe@acme.com OR email=jdoe@internal.acme.com.
Property Name | Type | Mandatory | Description |
|---|---|---|---|
- | YES | The list of attributes participating in the Correlation process, see Attribute Correlation Definition. Must contain at least one element. If the list contains several attributes they are ANDed together such as to produce: |
attributeCorrelationDefinitions properties
The configuration of the attribute mapping used to correlate an application account with a object(s).
Property Name | Type | Mandatory | Description |
|---|---|---|---|
inputAttributeId |
| YES | The input application account's attribute id (e.g. "uid" for a LDAP account) whose value must match a target Object attribute. Available attributes also include "built-in attributes", that must be configured using their armored format, e.g. "__objectId__". The list of built-in attributes is provided in a later section. |
idmAttributeId |
| YES | The target object attribute name (e.g. "login") whose value must match the value of |
normalizeRule |
| NO | Optional: a Normalize Rule used to transform the input value before comparing it with an IDM object attribute. The Normalize Rule will be typically executed with a Groovy script. |
customCorrelationStrategyDefinition properties
A Compute Rule is evaluated to produce a CorrelationResult. The Compute Rule will be typically executed with a Groovy script performing the complex business search(es)
using a ObjectFinder available in the Groovy Context.
Property Name | Type | Mandatory | Description |
|---|---|---|---|
computeRule |
| YES | The Compute Rule returning |
reactionDefinitions properties
Property Name | Type | Mandatory | Description |
|---|---|---|---|
reactionDefinition |
| NO | Configuration of the reaction to a synchronization situation. |
reactionDefinition properties
Each reactionDefinition will have the following configuration:
Property Name | Type | Mandatory | Description |
|---|---|---|---|
name |
| NO | An optional name only used to enhance the configuration display in the admin console GUI. |
situation |
| YES | The synchronization situation triggering this reaction ("unmatched", "linked", etc.) The possible values are listed in Synchronization Situations. |
actions | - | NO * | The list of actions to apply in reaction to |
Synchronization Situations
A synchronization event is categorized into a synchronization situation (or simply "situation"). Determining a situation is important because reactions may be configured.
The situation deals only with the existence or non-existence of an application account (e.g. a LDAP account), and with ownership of the account by an IDM object. In other words, it deals only with "links": an account is linked to an IDM object. It does not deal with the legality of the account (whether an IDM Identity should have an LDAP account). The situation also does not deal with changes in account attributes, this is the role of the "reaction".
The situation is evaluated by the correlation process, consisting in finding potential IDM owner(s) for the account (more on that later).
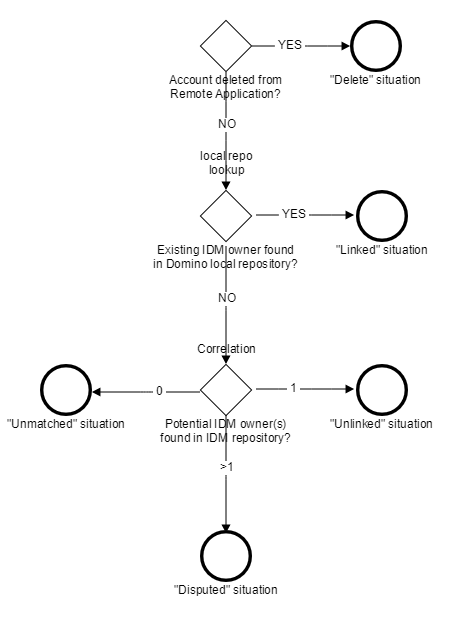
The following algorithm is used to determine a situation:
if the account has been deleted then the situation is "deleted"
the account's owner is looked up in the internal Synchronization service repository. If an owner is found then the situation is "linked"
if there is no current IDM owner referenced in the Synchronization service repository then the correlation is used to determine potential IDM owner(s) for the account. If potential owner(s) are found, the situation is either:
"unlinked" (single owner)
"disputed" (several owners)
no owner found: the situation is "unmatched"
The list of possible situations is summarized in the following table:
Situation | Description | Examples |
|---|---|---|
| Nominal case: an account is linked to an IDM object. They are synchronized. | An attribute of a remote application account was changed and it is reflected to the owning IDM object. |
| An account is found on the remote application, the correlation process determines exactly one existing IDM owner for that account, and the IDM owner does not have the account linked (yet) | The IDM repository is already populated with IDM objects and a new application whose repository is also already populated with accounts is registered to Synchronization service. |
| An account does not exist on the remote application anymore. It is still referenced in Synchronization service’s internal repository but no account in the remote application matches it. | A legal account is manually deleted on the remote application. |
| An account is found on the remote application, and no matching IDM owner was found for the account by the correlation process. | Initial import, or the account was created on the remote application using native administration tools. |
| An account is found on the remote application, and two or more potential IDM owners are found for it by the correlation process. | An ambiguous account is created manually on the remote application, e.g. using a login |
| Should never happen: the account is linked to two or more IDM objects. | Bug or inconsistent database. |
Reactions to Synchronization Situations
Once a synchronization situation has been determined, reaction(s) happen. Reactions are configurable. Several reactions may be associated with a given situation.
When the synchronization task type is "import", the reaction is always forced to "add an IDM object". To implement a more flexible behavior, where for example it is not desired to create new IDM objects but only update existing ones, just configure a synchronization task of type “reconciliation”, and configure a “NO_OP” reaction to the “DELETED” situation.
The list of possible reactions of class SyncAction is summarized in the following table:
Reaction | Description | Compatible Situations | Examples |
|---|---|---|---|
| Reflect the account changes to the corresponding existing IDM object |
| An attribute of a remote application account was modified by a local application's administrator. |
| Add an IDM object |
| Initial import. |
| Remove an IDM object |
| When an application account is deleted then the corresponding IDM owner must also be deleted. |
| Inactivate an IDM object |
| When an application account is deleted then the corresponding IDM owner must be deactivated. |
| Soft delete an IDM object |
| When an application account is deleted then the corresponding IDM owner must be soft deleted. |
| Add an account on the remote application |
| An account was accidentally deleted by a local application's administrator; it must be re-created. |
| Remove an account from the remote application |
| "Unmatched" and "unlinked": Non authoritative application. An "illegal" account was created on the Application using native administration tools. "Disputed": remove ambiguous application accounts that were created manually on the Application. |
| Inactivate an account on the remote application |
| Idem above. |
| Link (i.e. mark as "synchronized") an account and an IDM object |
| An existing application account and a matching IDM owner have been created separately in their respective repositories, but they were not synchronized. They will be now. |
| Unlink (i.e. mark as "not synchronized anymore") an account and an IDM object |
| An account was deleted on purpose by a local application's administrator; no further synchronization attempt should be performed anymore. |
| Do nothing, ignore the Shadow | N/A | Typically configured by an |
| Patch an IDM object (inbound case) or a remote application account (outbound case) |
| When an application account is deleted then the corresponding IDM owner must be patched. Do to this a configured custom action is applied. |
Some reactions are implicit, i.e. they occur even if they are not explicitly configured. For example, after a new application account has been successfully imported into the IDM, i.e. a new IDM object has been created, the application account and the IDM object are linked.
synchronizationActionDecisionDefinition properties
Pertains to the inbound case only. Enable to configure more finely the action(s) to execute during a synchronization task, namely according to the input data, instead of solely relying on SynchronizationReactionDefinition.
Property Name | Type | Mandatory | Description |
|---|---|---|---|
decisionRules |
| NO | Mutually exclusive with |
customDecisionRule |
| NO | Mutually exclusive with |
defaultActions |
| NO | Optional: the default action(s) to perform when no decision rule matches (see |
decisionRules properties
The content of an element of the decisionRules list field of a SynchronizationActionDecisionDefinition (see above section). It represents the configuration of a rule determining which synchronization action(s) to execute when the rule matches (see Synchronization Action Decision Definition).
Property Name | Type | Mandatory | Description |
|---|---|---|---|
actions | - | YES | The action(s) to perform when the rule matches, as a list of |
- | YES | The rule matching condition. |
Example of a SynchronizationActionDecisionDefinition with a custom Rule stating to do nothing (“no op”) if the IDM object does not possess “some_attribute”. If the IDM object possesses the attribute then it is synchronized as usual.
<synchronizationActionDecisionDefinition>
<customDecisionRule>
<script><![CDATA[if (IDM_OBJECT?.some_attribute) { return [] } else { return SyncAction.NO_OP }]]></script>
</customDecisionRule>
<decisionRules/>
</synchronizationActionDecisionDefinition>Example of a SynchronizationActionDecisionDefinition with a list of ActionDecisionRules. In this somewhat contrived example, if the last name of the IDM object matches “Doe”, then the IDM object is synchronized. No operation is performed otherwise.
<synchronizationActionDecisionDefinition>
<decisionRules>
<decisionRule>
<actions>
<action>SYNCHRONIZE_IDM_OBJECT</action>
</actions>
<objectMatchingCondition>
<objectKind>ACCOUNT</objectKind>
<objectTypes/>
<simpleObjectMatchingStrategyDefinition>
<inputAttributeId>lastName</inputAttributeId>
<regex>Doe</regex>
</simpleObjectMatchingStrategyDefinition>
</objectMatchingCondition>
</decisionRule>
</decisionRules>
<defaultActions>
<action>NO_OP</action>
</defaultActions>
</synchronizationActionDecisionDefinition>schemaMappingDefinition properties
Property Name | Type | Mandatory | Description |
|---|---|---|---|
- | YES | The list of attribute mapping configurations per Object Type. This list must contain at least one element. |
LDAP Provisioning Considerations
This section contains elements specific to the LDAP provisioning.
An LDAP entry possesses some "special" attributes:
DN
objectClass
When provisioning an LDAP entry, those 2 attributes must be set. They have specific target mapping names, imposed by the Evolveum LDAP connector conventions (see table below). Other LDAP attribute mappings, such as "givenName" or "uid", have the usual target names, such as "givenName" or "uid".
LDAP Attribute | Target Attribute Mapping Name | Attribute Mapping Example |
|---|---|---|
DN |
|
CODE
Where |
objectClass |
| If a provisioned LDAP entry should have the objectClass attribute multi-valued as:
then the following attribute mapping must be configured:
CODE
Note that this list does not contain the main
CODE
|
Example
Here is an XML representation of an Application.
