Application Profile
An Application Profile targets a specific Application, e.g. the "Trade" Active Directory. Having an Application Profile always implies having an account on the target Application.
Definition
An Application Profile targets a specific Application, e.g. the "Trade" Active Directory. Having an Application Profile always implies having an account on the target Application (this is implicit), but the Application Profile also configures all the "Entitlement" Assignments (e.g. the asset associations) that are possible for the Application, in terms of group membership and/or privilege attribution. “Entitlements” can thus be assigned to a provisioned account. Typically, for the LDAP directory case, an Entitlement is a LDAP group. Upon account provisioning, group membership is enforced, according to configured rules.
To sum up, if an Application internally manages a set of groups and/or privileges (i.e. Entitlements), a set of Assignments can be configured to represent the possible associations of user accounts with those entitlements, as illustrated below:
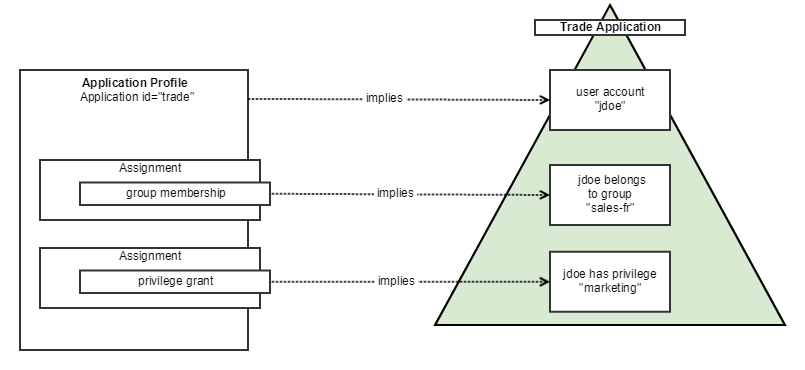
ApplicationProfiles are conditionally associated with IDM objects, such as IDM Identities or IDM Organizations. A profile association is conditional, because an IDM object must match an ApplicationProfile’s Object Matching Condition to be provisioned on a target Application. If the ApplicationProfile matches, then the account is provisioned on the target Application, and Entitlements (if any) are assigned to the account.
The next section details this.
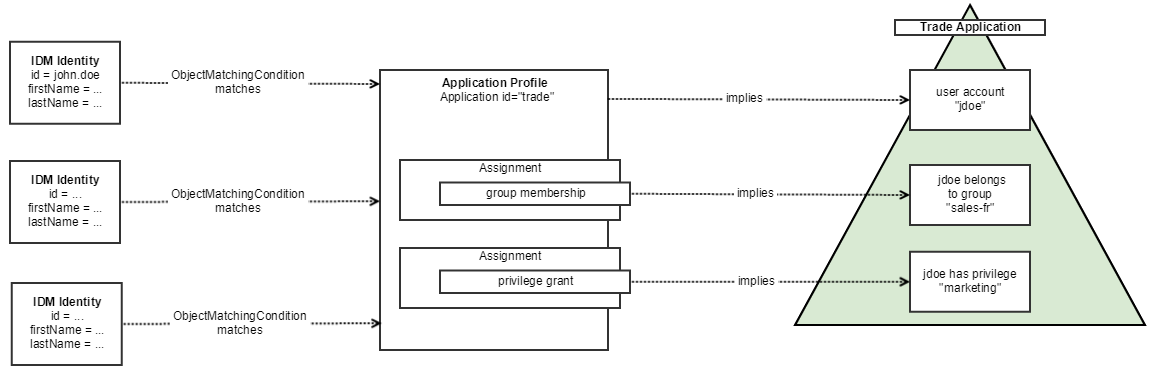
Configuration
You can access the Application Profiles configuration :
by clicking on "Synchronization" → "Application Profiles"
by clicking on "System" → "Configurations"->”Synchronization Service” and perform an import/export.
Properties
The possible ApplicationProfile configuration elements are :
Property Name | Type | Mandatory | Description |
|---|---|---|---|
id |
| YES | The Application Profile identifier. |
name |
| YES | The Application Profile name. |
description |
| NO | The Application Profile description. |
| NO | A list of Assignments enabling to associated Entitlements (groups, privileges) to a provisioned account. See next table for more information. | |
applicationId |
| YES | The id of the target Application. |
enabled |
| YES | The Application Profile status. Default value : true |
| YES | A condition ObjectMatchingCondition determining whether an IDM object should have the ApplicationProfile or not, e.g. be provisioned on the target Application. An | |
shadowKind |
| YES | ACCOUNT, ORGANIZATION, RESOURCE, ROLE, ROLE_PUBLICATION, ENTITLEMENT |
Assignment properties
Property Name | Type | Mandatory | Description |
|---|---|---|---|
entitlementsSearchRule |
| YES | How to search on the remote Application the Entitlement(s) to be assigned to the account. This is a The list of Entitlements to be found can be constructed dynamically, typically by listing the roles of a provisioned IM object. |
association |
| YES | The name of the
|
entitlementsSearchBase |
| NO | A search base for entitlements. If not specified, entitlements are searched from root. |
matchingCondition |
| NO | A "matching condition" indicating whether this assignment should be applied or not on the account. If null then this assignment is always applied. |
detectIllegalEntitlements |
| NO | Whether to detect "illegal" Entitlements, given outside Memority's jurisdiction. Those are Entitlements that have been given to an account by a local Application administrator, and they do not match If
|
illegalEntitlementsFilterRule |
| NO | An optional rule enabling to ignore some Entitlements given outside Memority’s jurisdiction. It is an additional "programmatic" filter applied on the Memority side (not on the remote application), enabling to further refine the list of illegal entitlements, using elaborate criteria that are not natively supported by the remote application. For example, in the LDAP case, such a criterion could be "group DN does not end with ou=technical-groups,dc=memority,dc=com" This is a |
