Adaptive Authentication
My-Access provides Adaptive Authentication mechanisms to select the best authentication methods based on predetermined rules defined by administrators.
In order to adapt authentication levels, Adaptive Authentication relies on existing user data such as:
User attributes (e.g. identity type, user role)
Level of security defined in Memority for the federated application the user is trying to access
Level of security defined in Memority for authentication means activated for the tenant
Memority credentials activated for the current user (e.g. user has enrolled Memority OTP browser/mobile, Memority password)
User device type (User agent)
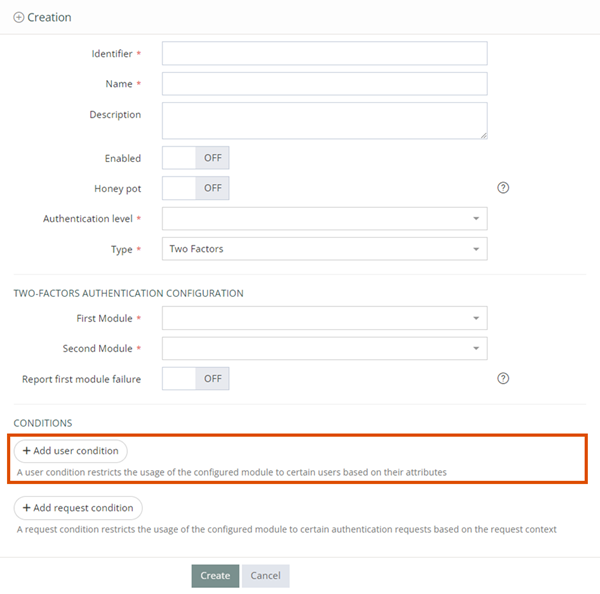
Configuration page for new authentication methods
For example, leveraging user conditions, My-Access can segregate internal users and external users and suggest different authentication mechanisms:
If the user is INTERNAL → Require authentication via password (+ Yubikey for critical applications)
Inf the user is EXTERNAL → Require authentication via password + email OTP to partner’s email address (and deny access to critical applications)
Memority can select transparent authentication methods (such as Windows Transparent Authentication/Kerberos) and fallback to explicit user-specific authentication methods in case of failure.
Adaptive Authentication is very effective to offer seamless authentication to your workforce (employees, partners and suppliers). Check our Risk-Based Authentication capabilities for our consumer-oriented solutions.
