Risk-Based Authentication
Risk-Based Authentication (RBA) is an adaptive security mechanism which evaluates the trustworthiness of every login in real-time.
RBA generates a risk score based on the login context and requires the user to meet a minimum authentication level based on the configured policies. Then, it filters the available authentication mechanisms based on the associated risk.
The Value of Risk-Based Authentication
Traditional authentication applies the same mechanisms to every user. At the same time, it creates friction for legitimate users by repeatedly asking them to verify their identity in low-risk situations.
RBA adjusts the authentication mechanisms to align with the risk level of each user. This approach allows to protect user accounts against compromise and keep the access smooth for legitimate users.
Here are the main benefits of RBA:
For the company
Stronger security. RBA challenges suspicious logins and prevents data breaches as a result.
Remote work compatibility. In hybrid and remote environments, RBA protects users' access from any location by adapting the authentication level to the context of each login.
For the user
Better user experience. With RBA, users get frictionless in low-risk situations.
Customizable authentication workflows. Users benefit from flexible login experiences, with additional verification steps only when needed.
Increased trust. Users feel confident that their accounts are protected.
How RBA Works
RBA evaluates the context of each login attempt and decides whether to grant access right away, request extra verification, or deny the access request. Contrary to traditional authentication RBA assigns a risk score that reflects how unusual or suspicious a login looks.
The system establishes the risk score based on device, location, IP address, and user behavior.
Example: A login from a trusted laptop at the office counts as low risk and allows seamless access. However, if the same account connects from a new device in another country, the risk score rises and the user must complete an additional verification step.
How Memority Implements RBA
Memority runs a dedicated RBA service that evaluates risk signals. The system applies a large bench of rules based on various attributes in order to establish a valuable risk score.
The system evaluates risk signals on the following levels.
Environment risk. Checks device attributes: IP address, browser, and whether the device is known or unknown.
User risk. Checks user behavior signals: last login time, location history, and unusual activity.
Authenticated risk. Lowers the risk score depending on the strength of the authentication mecanisms previously used by the user.
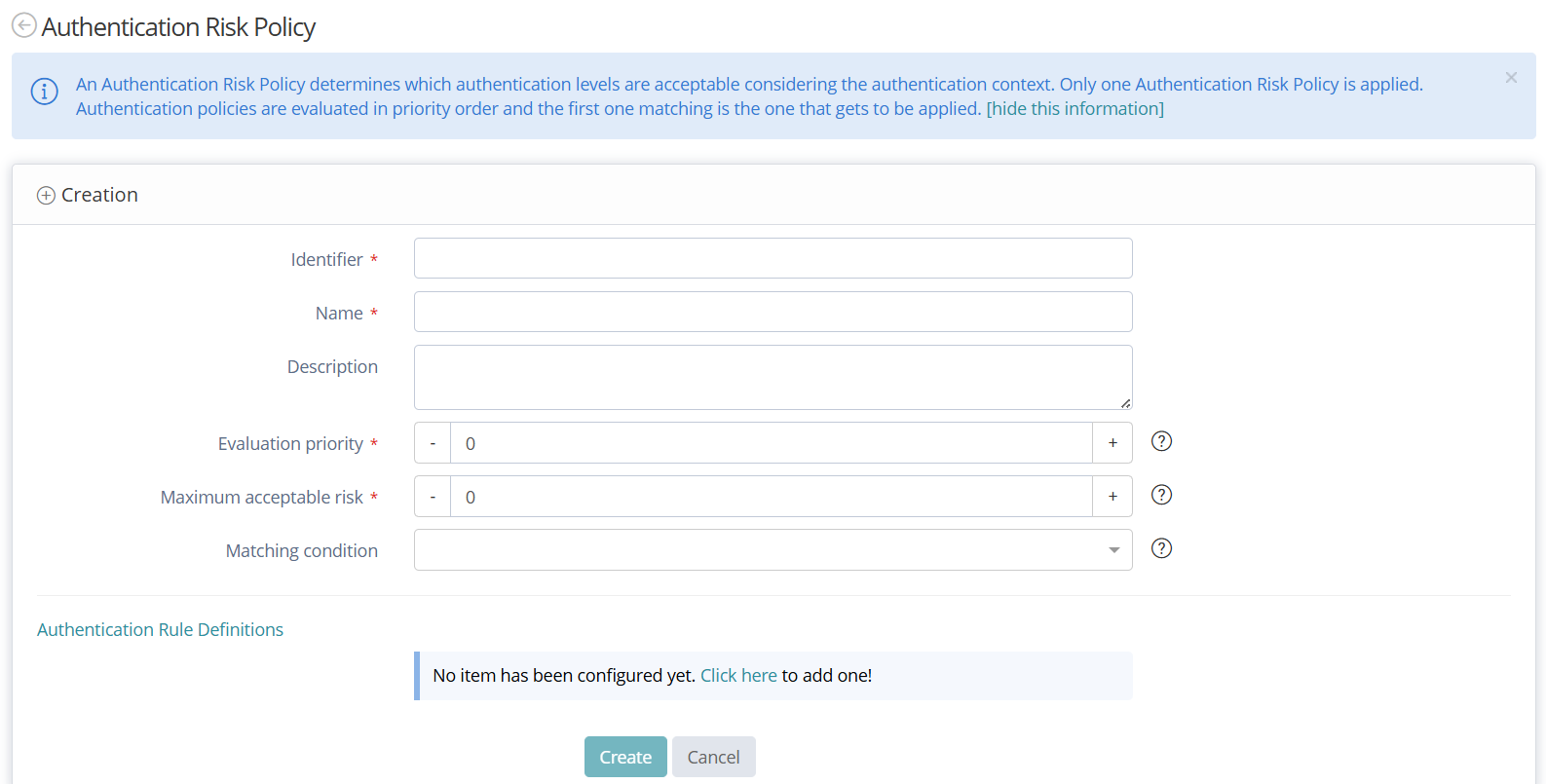
Authentication Risk Policy Creation
Risk evaluation:

Once Memority evaluates the risk signals, it compares the score against the configured threshold and follows this logic:
If the score falls below the threshold, Memority accepts the authentication, finalizes the login and redirects the user to the application without asking for additional verification steps.
If the score rises above the threshold, Memority enforces step-up authentication, such as a one-time password or another strong factor.
If the score is extremely high, there is an option to fully block the authentication process.
Risk-Based Authentication is a powerful tool which allows organizations enforce their adaptive authentication and prevent data breaches while keeping the user experience smooth.
