Federation
Definition
A Federation is a configuration allowing an application to be integrated with Memority using standard federation protocols such as SAML, WSFederation, OAuth2 or OpenID Connect.
A Federation configuration applies on a Resource (an application in this context).
Configuration
The following widgets must be configured to be able to configure the Federation and see the associated logs :
Federation Widget : to see the Federation tab on a Resource allowing you to do the Federation configuration
Federation Logs Widget : to see the Logs tab on a Resource allowing you to see debug logs associated to this Federation configuration
Usage
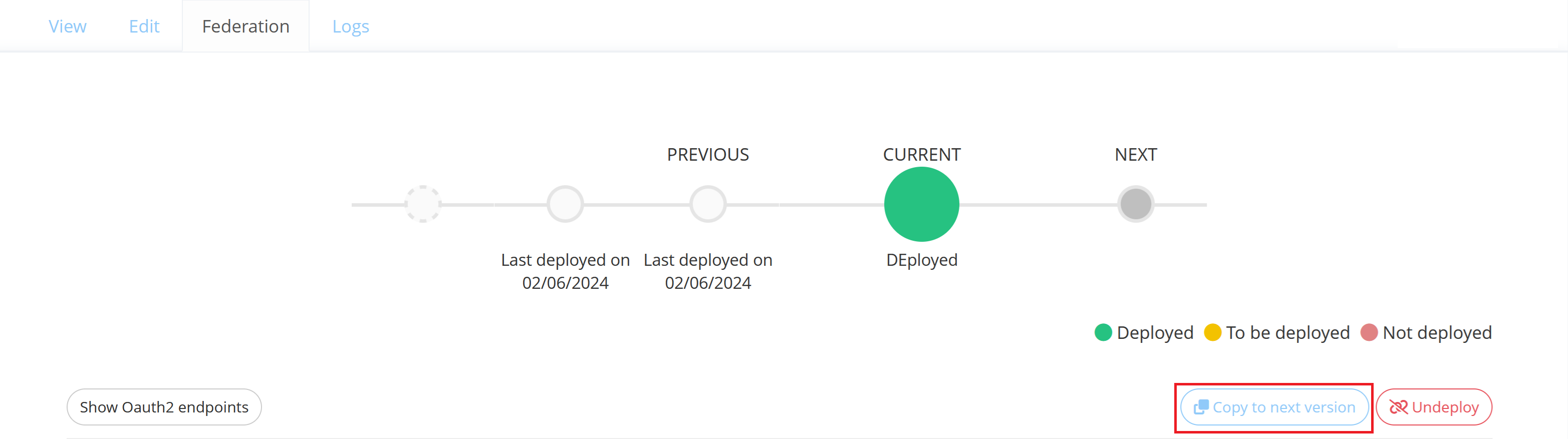
Create and update a Federation
You can create a Federation configuration on a Resource by clicking on the Create button of the desired type of federation (SAML, WSFED or OAuth2/OIDC) in the “Federation” tab.

You can update a Federation configuration on a Resource in the “Federation” tab by clicking on the "Copy to next version" button.
SAML Federation
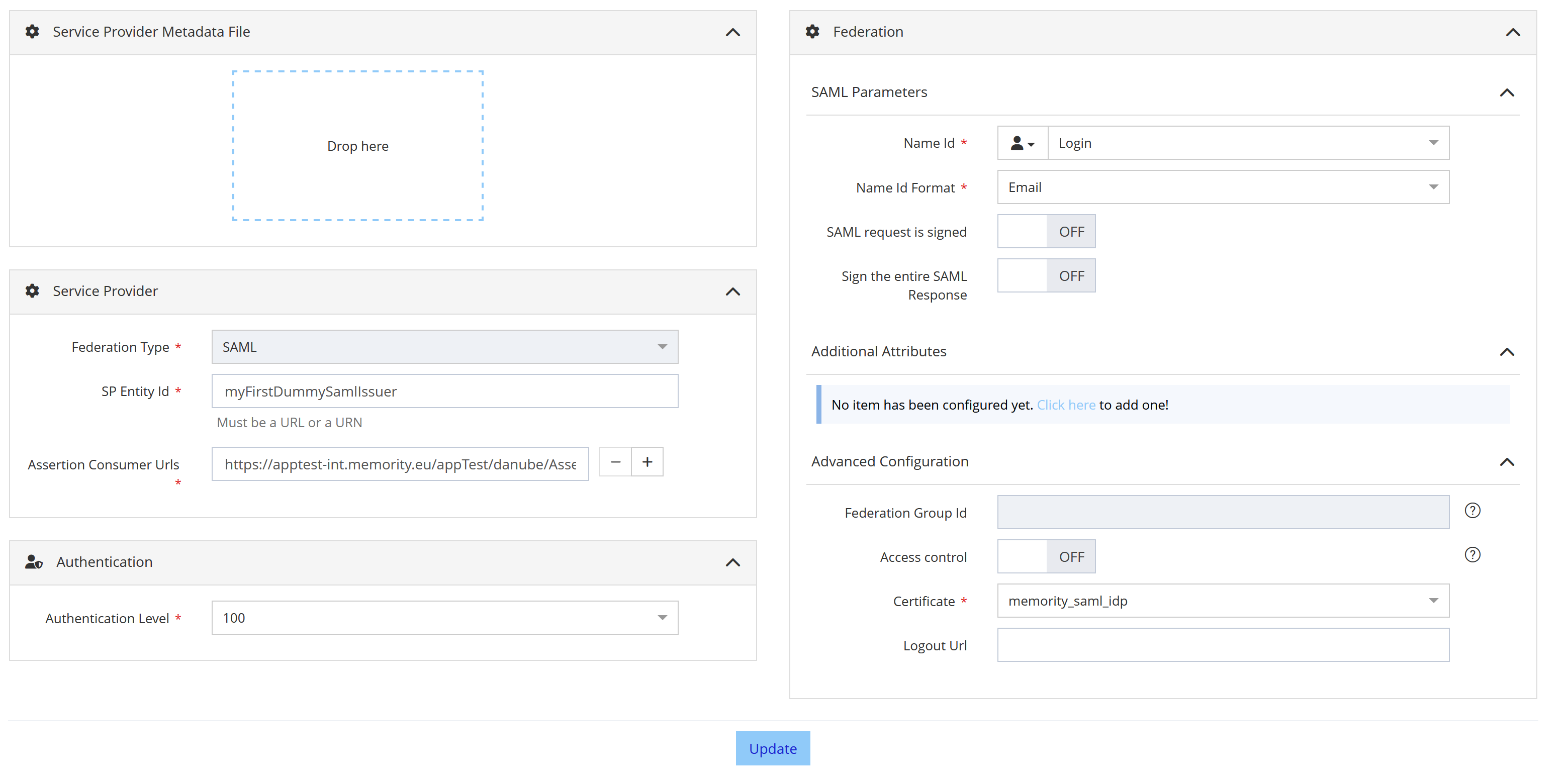
Configuration screen of a SAML Federation
The following properties should be filled for a Federation of type SAML :
Property name | Mandatory | Description | Comments |
|---|---|---|---|
Service Provider Metadata File | NO | Metadata file of the Service Provider. | If provided, data contained in the metadata file will be used to pre-fill some Federation properties (SP entityID, ACS URL, …). |
SP Entity Id | YES | The EntityID of the Service Provider. | May be imposed by the Service Provider. |
Assertion Consumer Urls | YES | The SP Url that will consume the SAML assertion. | Several Assertion Consumer Urls can be configured. It is recommanded that these URLs be in HTTPS. |
Authentication Level | YES | The authentication level required to access the application. | Only authentication levels declared in settings are available in the list. |
Name Id | YES | Value sent as NameID in the SAML assertion. | Can be a user attribute, an Attribute Function or a constant. Click on the icon to select the good type. |
Name Id Format | YES | Format of the NameID sent in the SAML assertion. | Choose the one supported by the Service Provider. |
SAML request is signed | NO | Indicate if the SAML request signature is required and must be verified. | Disabled by default. |
SAML request signing certificate | NO | Certificate public key of the Service Provider in PEM format. Used to verify the SAML request signature. | Only visible if “SAML request is signed” is enabled. |
Sign the entire SAML response | NO | To sign the entire SAML response and not only the SAML assertion. | Disabled by default. |
Additional attributes | NO | User attributes to be sent in the SAML assertion. | Can be user attributes, Attribute Functions or constants. Click on the icon to select the good type. |
Access control | NO | When enabled, only users having the right app.access.<resource_id> can access the application. | Disabled by default. |
Certificate | YES | Certificate used to sign the SAML assertion. | Only certificates configured for the tenant are available in the list. A default signing certificate for SAML federations can be declared in settings. |
Logout Url | NO | Logout Url used to terminate the user SSO session in a SAML logout use case. | - |
WSFED Federation
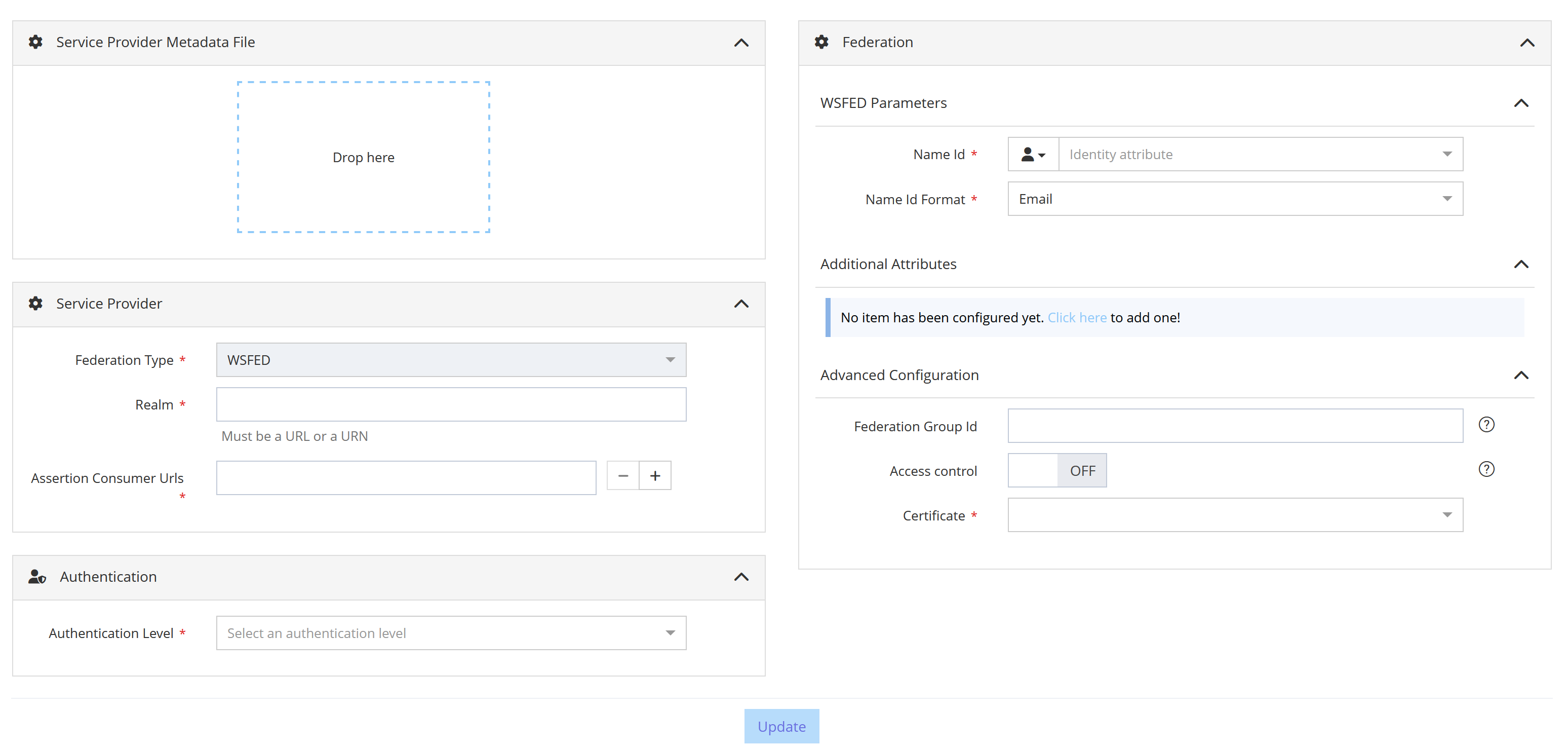
Configuration screen of a WSFed Federation
The following properties should be filled for a Federation of type WS-Federation :
Property name | Mandatory | Description | Comments |
|---|---|---|---|
Service Provider Metadata File | NO | Metadata file of the Service Provider. | If provided, data contained in the metadata file will be used to pre-fill some Federation properties (SP entityID, ACS URL, …). |
Realm | YES | Unique identifier of the Relying Party. | May be imposed by the Relying Party. |
Assertion Consumer Urls | YES | The SP Url that will consume the WSFederation assertion. | Several Assertion Consumer Urls can be configured. It is recommanded that these URLs be in HTTPS. |
Authentication Level | YES | The authentication level required to access the application. | Only authentication levels declared in settings are available in the list. |
Name Id | YES | Value sent as NameID in the WSFederation assertion. | Can be a user attribute, an Attribute Function or a constant. Click on the icon to select the good type. |
Name Id Format | YES | Format of the NameID sent in the WSFederation assertion. | Choose the one supported by the Service Provider. |
Additional attributes | NO | User attributes to be sent in the WSFederation assertion. | Can be user attributes, Attribute Functions or constants. Click on the icon to select the good type. |
Access control | NO | When enabled, only users having the right app.access.<resource_id> can access the application. | Disabled by default. |
Certificate | YES | Certificate used to sign the WSFederation assertion. | Only certificates configured for the tenant are available in the list. A default signing certificate for WSFed federations can be declared in settings. |
OAuth2/OIDC Federation
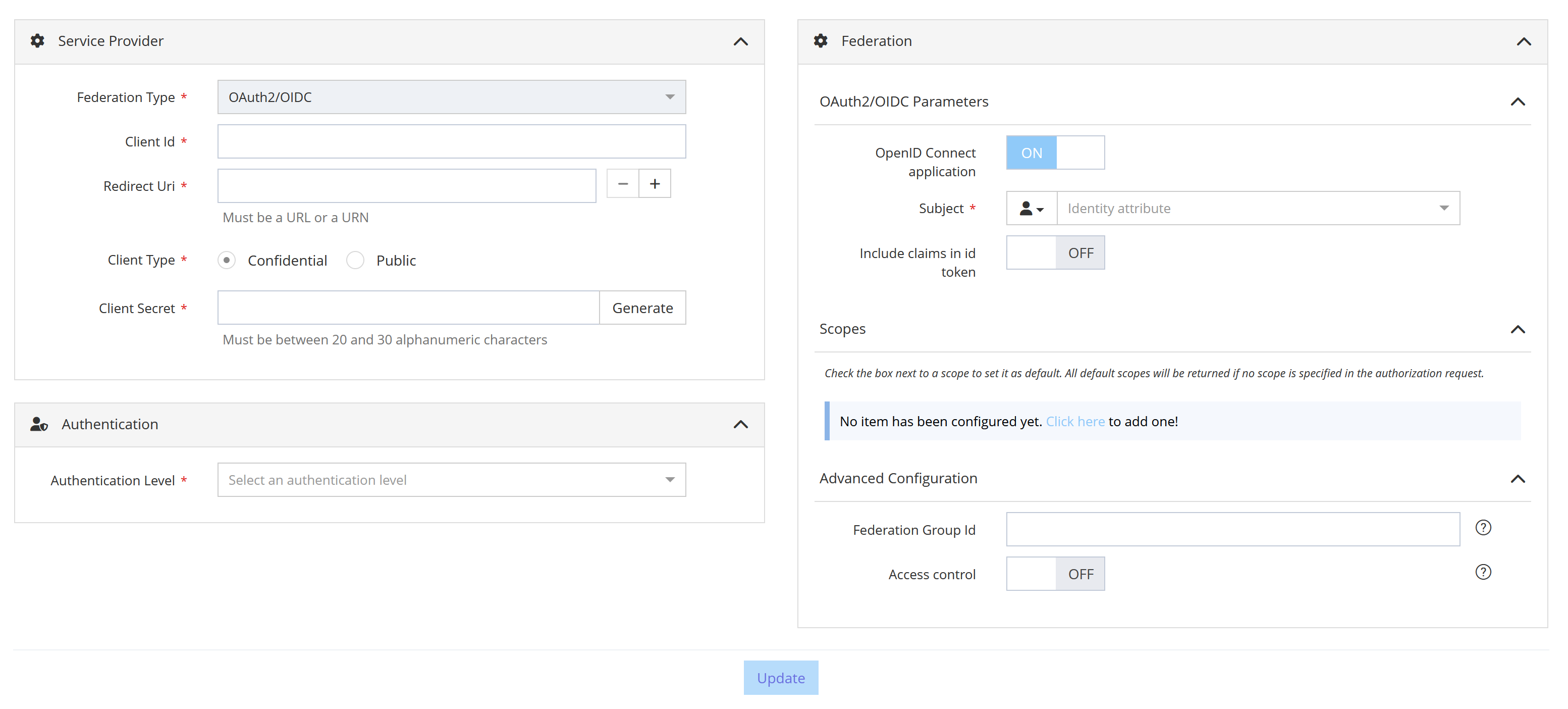
Configuration screen of an OAuth2/OIDC Federation
The following properties should be filled for a Federation of type OAuth2/OIDC :
Property name | Mandatory | Description | Comments |
|---|---|---|---|
Client Id | YES | Unique identifier of the OAuth2/OIDC client application. | May be imposed by the client application. |
Redirect Uri | YES | The application Uri that will receive the OAuth2/OIDC tokens. Should be an URL or an URN. | - |
Client Type | YES | The OAuth2/OIDC client type. | Must be |
Client Secret | YES | The client secret associated to the Client Id. | Only required for |
Authentication Level | YES | The authentication level required to access the client application. | Only authentication levels declared in settings are available in the list. |
OpenID Connect Application | NO | Indicates if the application is an OpenID Connect application. | Set it to ON for an OpenID Connect application and to OFF for a simple OAuth2 application. |
Subject | YES | Attribute value sent as Subject in the id token. Only available for an OpenID Connect application. | Can be a user attribute, an Attribute Function or a constant. Click on the icon to select the good type. |
Include claims in id token | NO | To include all configured scopes in the id token. Only available for an OpenID Connect application. | - |
Scopes | NO | User attributes returned as scopes. Check the box next to the scope to define it as default scope. Default scopes are returned in the authorization response if no scope is requested by the application. | Can be user attributes, Attribute Functions or constants. Click on the icon to select the good type. |
Access control | NO | When enabled, only users having the right app.access.<resource_id> can access the application. | Disabled by default. |
Read a Federation
You can consult a Federation on a Resource by clicking on the "Federation" tab.
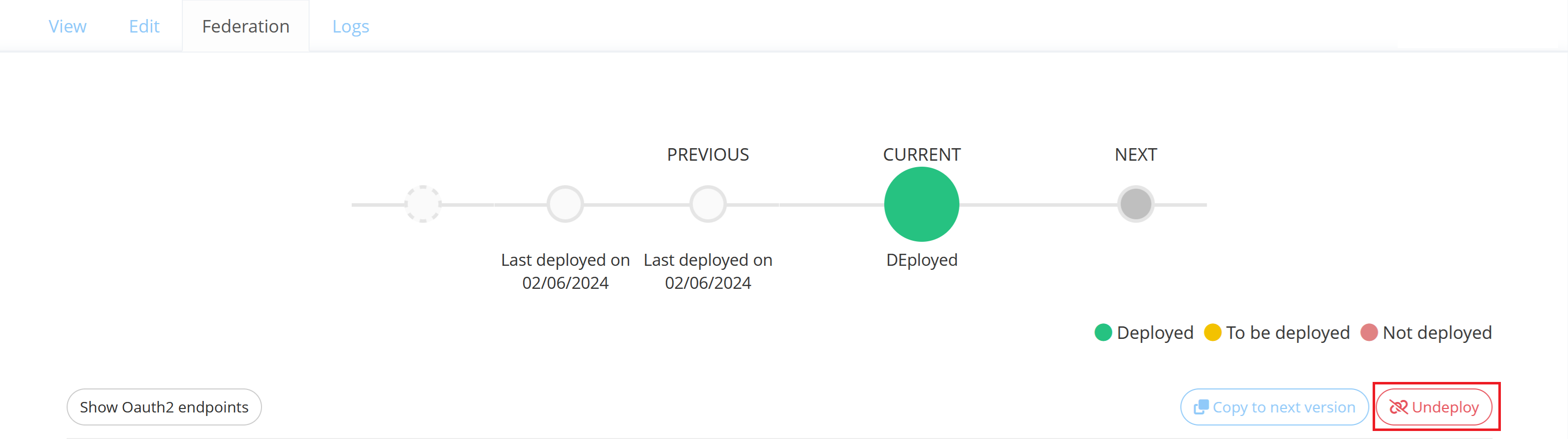
Undeploy a Federation
You can undeploy a Federation on a Resource by clicking on the "Undeploy" button in the “Federation” tab.
When undeployed, the Federation is still visible in the Memority portal but can not be used anymore.
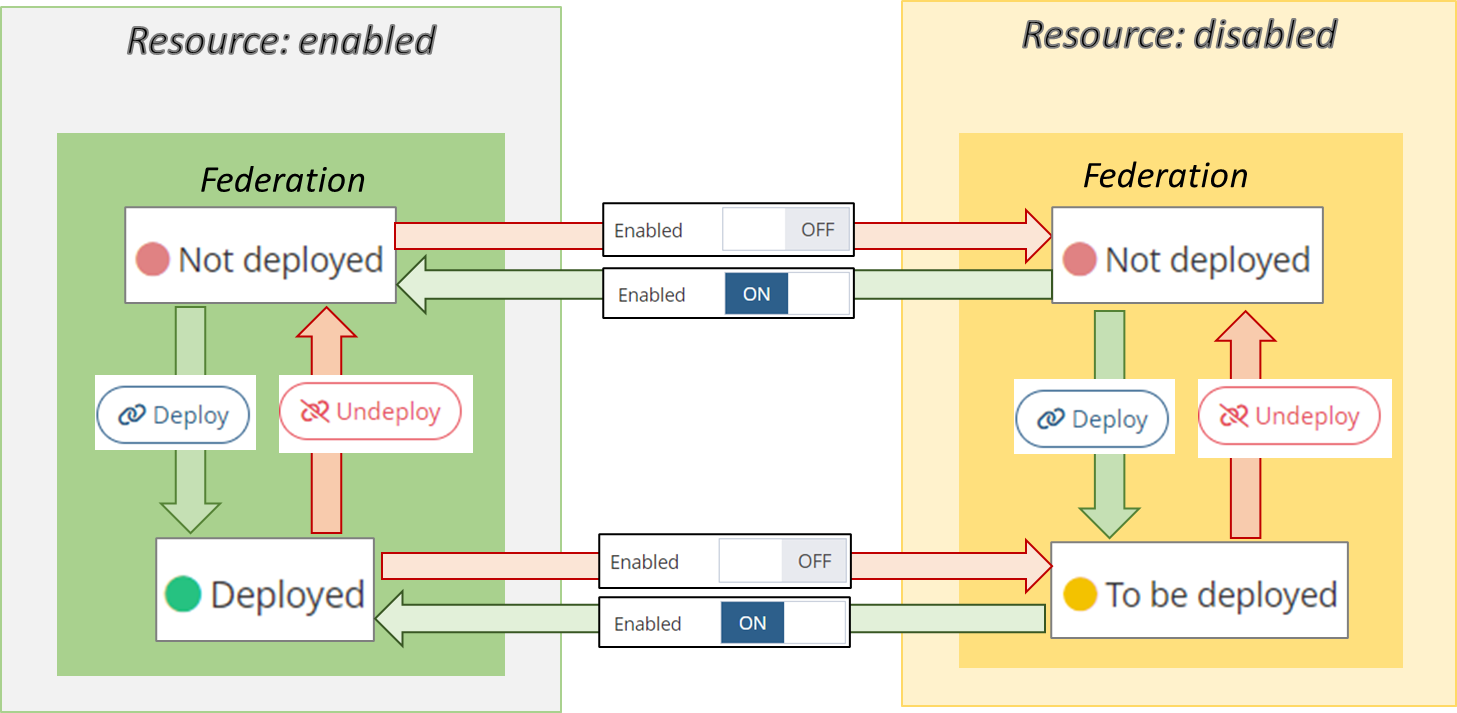
Understand Federation statuses
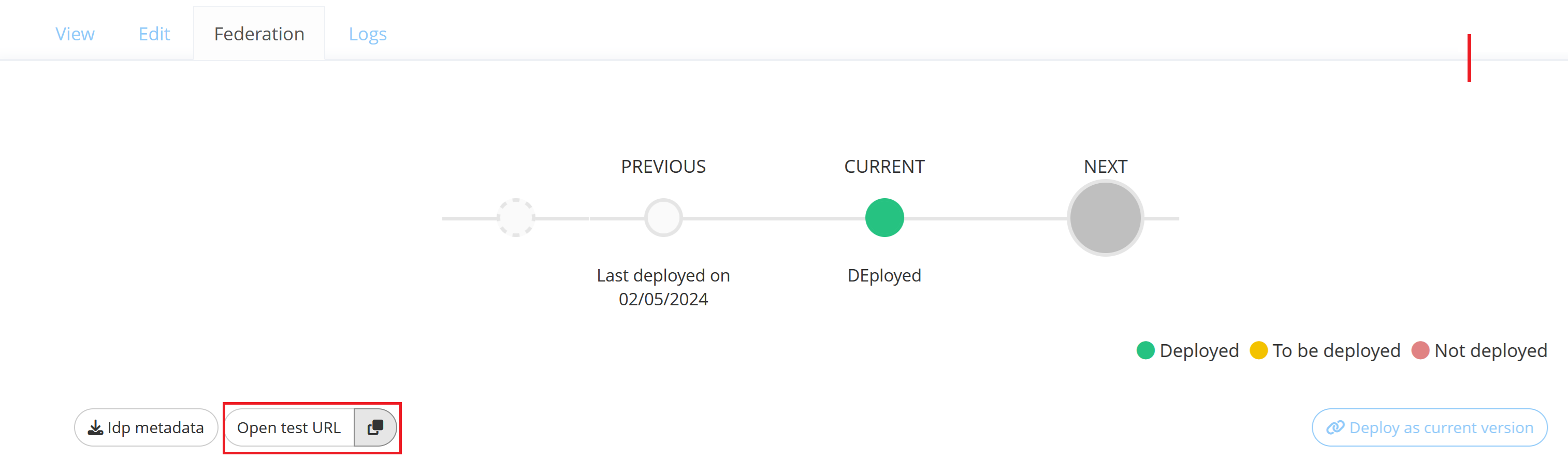
A Federation can have 3 different statuses that apply to its CURRENT Version :
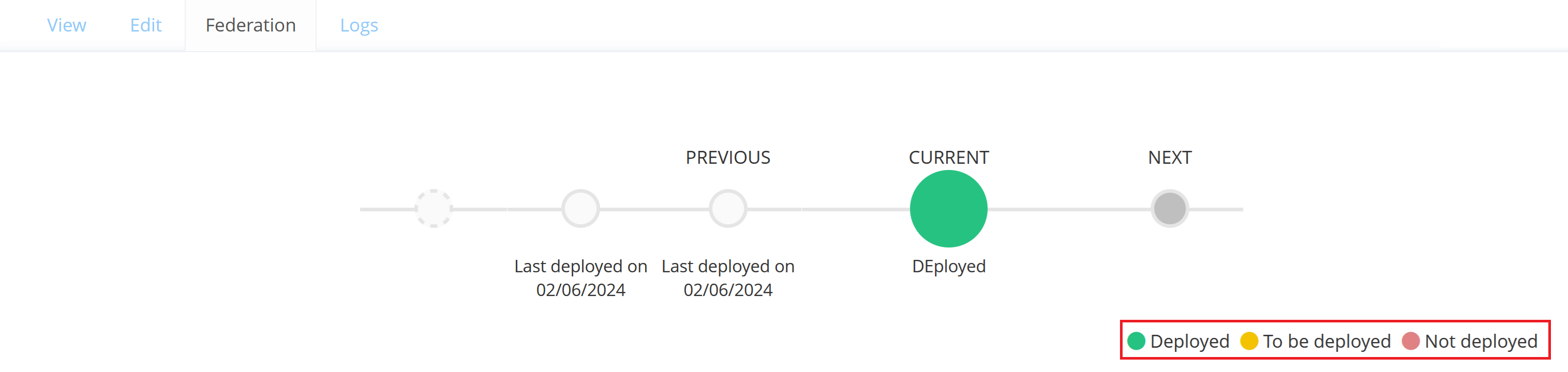
Deployed : The Federation of an enabled Resource is deployed on Memority and is ready to use.
To be deployed : The Federation is not deployed on Memority as the Resource is disabled. Will automatically become deployed after enabling the Resource.
Not deployed : The Federation is not deployed on Memority and cannot be used.
The following diagram explains how a Federation can reach these 3 statuses :
Get the Memority configuration for a Federation
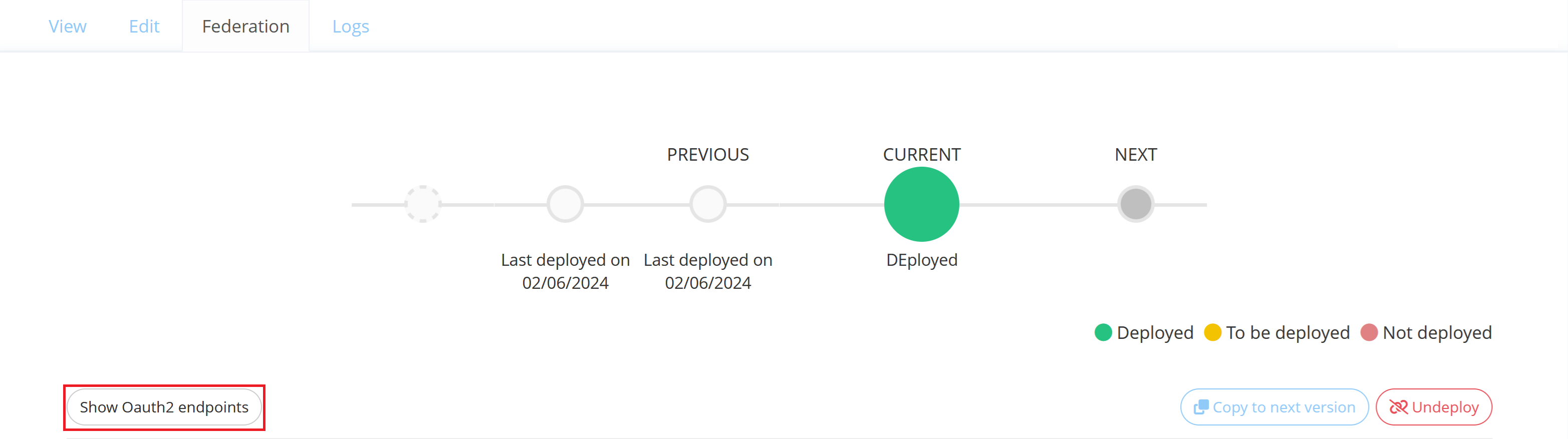
OAuth2/OIDC Federation
You can view Memority OAuth2/OpenID Connect endpoints by clicking on the “Show oauth2 endpoints” button on the OAuth2/OIDC Federation.
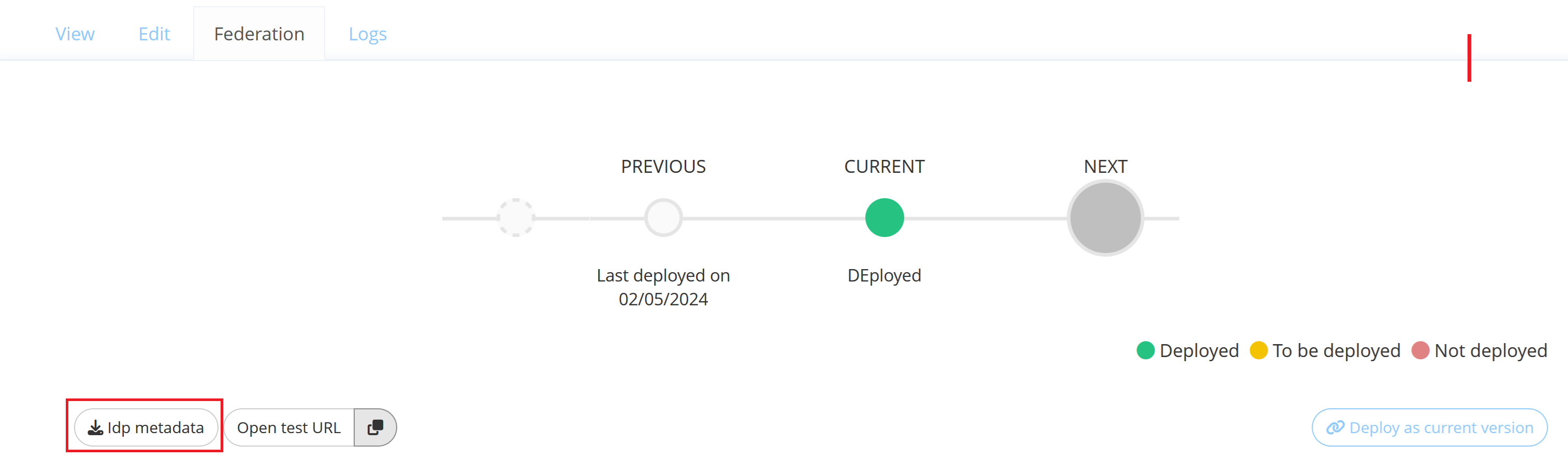
SAML/WSFED Federation
You can download the Memority IdP metadata by clicking on the “Idp metadata” button on the SAML/WSFED Federation.
Test the configuration
Only for SAML and WSFederation applications.
Once the federation configuration is successfully deployed, you can test it in “IdP-initiated” mode by clicking on the “Open test URL” button.
Debug logs
Debug logs related to a Federation configuration are available through the Logs tab on the Resource.
See Federation Logs Widget to configure federation debug logs.
Reporting
All Federations configurations are provisioned to a Federation Mongo collection.
It allows you to see all modifications done on the Federation or to identify all applications using a specific Attributes Function for example.
Read Next
- Access Attributes
Access Attributes Definitions define attributes that can be used for authentication and in application’s federations.
- Attribute Functions
Attribute Functions allow you to evaluate and manipulate attributes to be sent to applications through a Federation.
- Federation Logs Widget
The Federation Logs Widget allows to view logs related to a Federation.
- Federation Widget
Allows to manage or display the Federation corresponding to an application Resource.
- OAuth2
OAuth2 configuration allows to define some global parameters that will apply to all OAuth2/OpenID Connect federations of the tenant.
- Reporting Object Configurations
Reporting Objects define how one may interact with an underlying (built-in or custom) Document Collection.
