2025-07
NOT DEPLOYED / DEPLOYED IN STAGING / DEPLOYED IN PROD
2025.07.21 - My-Identity
AWS-PARIS AWS-DUBLIN S3NS
This new release brings improvements to the Import Feature
Delivery Timeline
Staging:
Production:
Import Feature Improvements
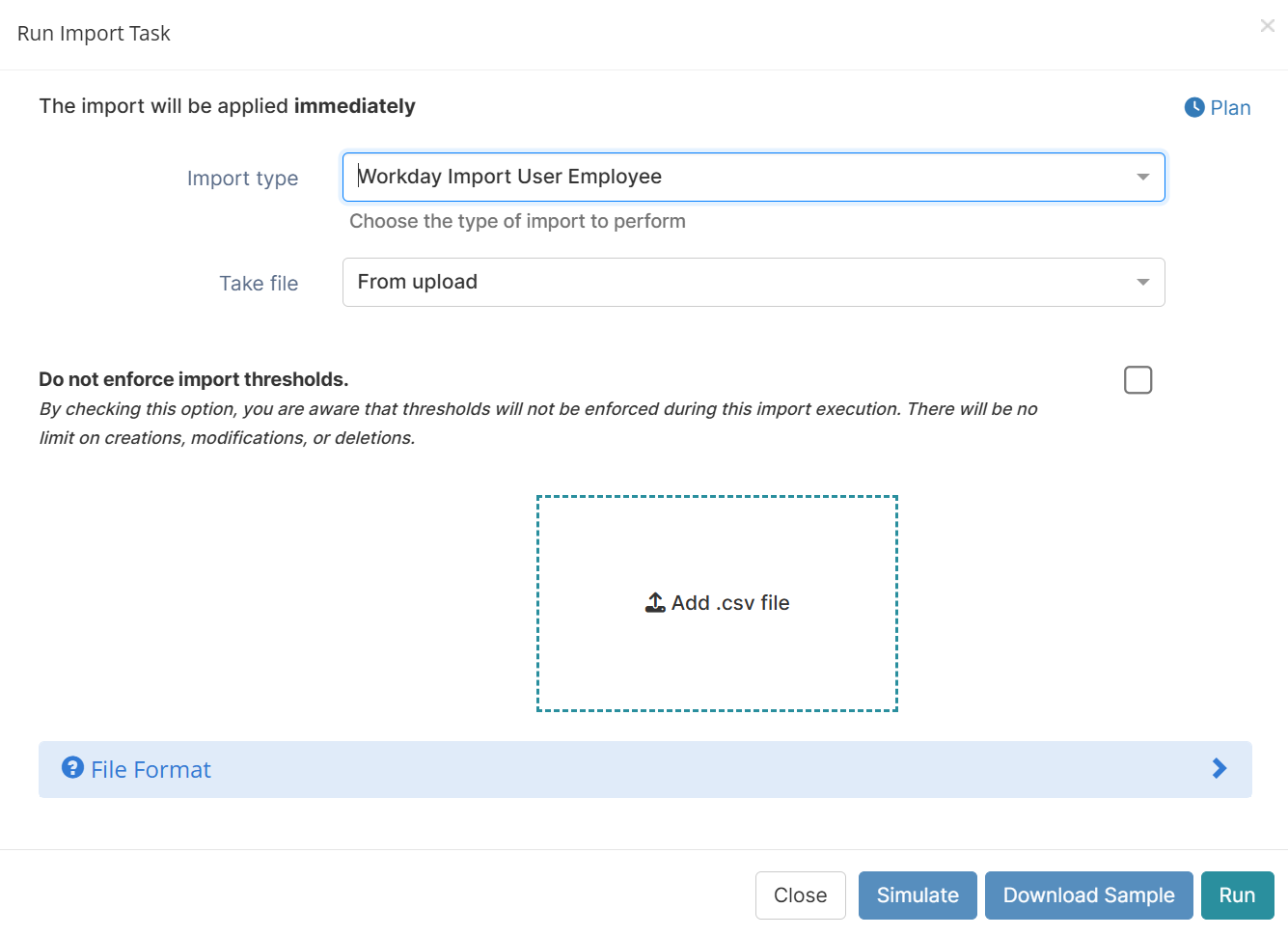
We’ve improved the Import feature to give you more control and flexibility:
Choose how to import: Upload a CSV file or retrieve it directly from the Memority exchange server.
Expand your sources: Launch imports from LDAP, REST APIs, and other external sources, all within the same interface.
Override import thresholds: Admins can now bypass default limits when needed.
These ehnancements streamline your data onboarding process and give you more control over import operations.
Patches
MyMFA now whitelists by default.
Reworked the Memority Portal Loader.
Enhanced RGAA (accessibility) compliance.
Other technical updates.
2025.07.21 - My-Access
AWS-PARIS AWS-DUBLIN S3NS
This release improves Risk-Based Authentication (RBA) with better error handling, IP checks, network filtering, new admin menu, and fixes bugs for enhanced stability and security.
New Features and Improvements
RBA Fallback for Groovy Failures
Now, if a rule fails at runtime the RBA allows only authentication mechanisms with a level above a configurable threshold (default: 80).
To know more, see HandlingGroovyErrors.New Groovy Context Variable for Client IP Matching
You can now use theREQ.ipcontext variable in RBA rules to check if the client's IP address matches a specific range.
To know more, see RBA Rule Definition.Memority Integration Tool supports RBA
You can now configure and deploy on a tenant the RBA service. This feature is currently experimental.
To know more, see Memority Integration Tool.RBA Network filtering
We enabled network filtering for RBA.New Menu Entry for RBA Configuration
A new menu entry called Access Risk is now available in the administration portal to manage the RBA service. Access Risk includes the following sub-entries:
Sub-entries | Description |
|---|---|
The configuration of the access risk corrections allows the system to:
| |
An environment risk policy is a set of rules that computes the first risk score based on the user’s device (IP address, user-agent, last use date, etc). | |
A user risk policy is a set of rules based on the Identity’s activities (last authentication date, last location city, etc and the Environment risk. | |
An Authentication Risk Policy is a set of rules that defines the acceptable authentication mechanisms based on the authentication context. |
Patches and Performance Enhancements
Bug fixes
Fixed publishing of RBA artifacts to Maven Central.
Fixed security vulnerabilities in Groovy scripts.
Fixed an issue to ensure only Groovy scripts can define matching conditions in RBA rules.
